
If you have recently purchased a Trezor hardware wallet or you are considering enhancing the security of your digital assets, the official entry point is trezor.io/start. This guide will walk you through everything you need to know about using and setting up your Trezor wallet, from installation to safety best practices, and why Trezor remains one of the most trusted solutions for cryptocurrency storage.
Trezor is among the earliest and most reputable hardware wallets on the market. Developed by SatoshiLabs, this device protects your digital currencies against hacks, malware, and phishing attacks. While online wallets and exchange accounts can be compromised, a hardware wallet like Trezor keeps your private keys offline, ensuring maximum protection.
The official website trezor.io/start is where every new user should begin. This page ensures you are following the most up-to-date, official instructions directly from the manufacturer. By avoiding unofficial sites and tutorials, you protect yourself from counterfeit software and phishing attempts.
When you receive your Trezor wallet, you will notice that the packaging is carefully sealed. This tamper-evident design ensures the device has not been compromised. Inside the box, you will typically find the Trezor device, a USB cable, instruction cards, and most importantly, a recovery seed card.
Once unboxed, the next step is to connect your Trezor wallet to your computer using the supplied USB cable. You will then navigate your browser to trezor.io/start, where official setup tools and security instructions are provided. This eliminates the risk of downloading unverified software from other sources.
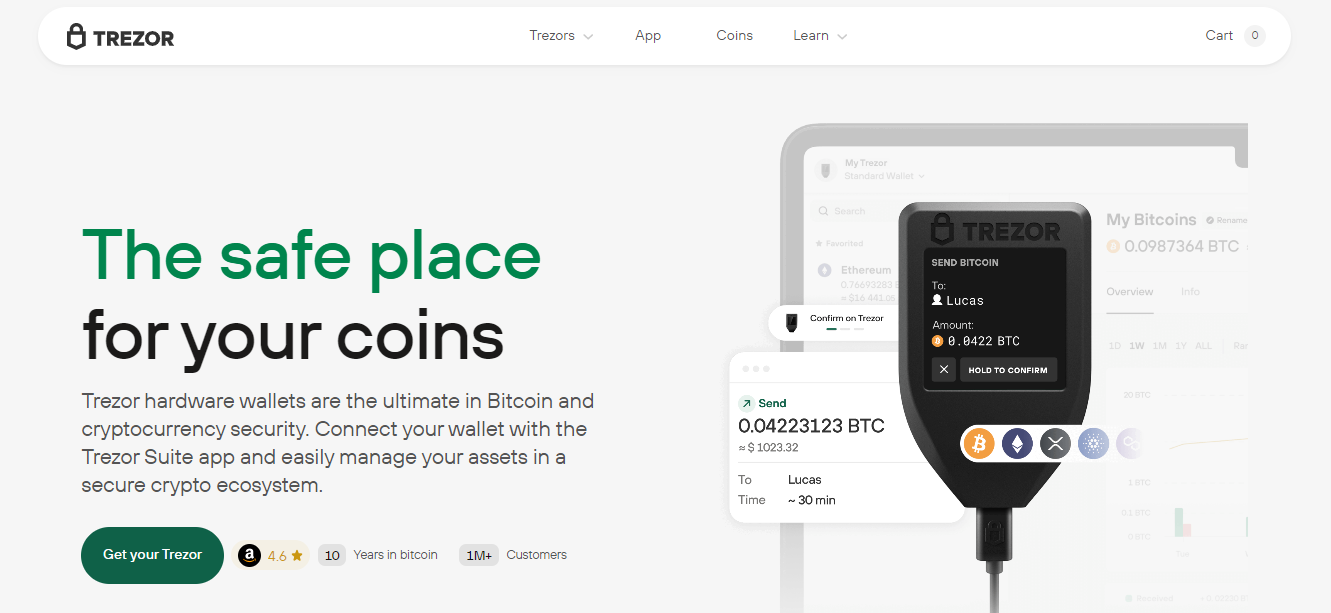
Trezor Suite is the official desktop and web application that allows you to manage your assets securely. After visiting trezor.io/start, you will be prompted to install Trezor Suite. The installation process is straightforward and available on Windows, macOS, and Linux.
Trezor Suite is not just a wallet interface. It offers advanced features such as transaction labeling, privacy settings, and integrated exchanges. Since the application is officially developed by Trezor, it undergoes strict security testing and frequent updates to keep your crypto safe.
When you first initialize your Trezor device, you will be prompted to create a new wallet. During this process, the device will generate a private recovery seed. This seed typically consists of 12 to 24 randomly generated words. Write these words down carefully on the supplied recovery sheet and store them in a secure, offline location. Never take a digital photo or store it on a computer.
The recovery seed is the single most important element of your Trezor wallet. If your device is lost or damaged, you can restore access to your funds using this seed. Conversely, if someone else gains access to it, they could access your assets. Therefore, safeguarding it is non-negotiable.
Once your wallet is set up, Trezor Suite allows you to send and receive various cryptocurrencies. Each time you initiate a transaction, confirmation must be made directly on your Trezor device, ensuring that no malicious actor can authorize a transfer without your explicit approval.
Trezor supports hundreds of digital assets, including Bitcoin, Ethereum, Litecoin, and many ERC-20 tokens. This makes it a versatile choice for investors who hold diverse portfolios.
Trezor goes beyond simple key storage. The Wallet includes PIN protection, passphrase setup, and secure firmware updates. Each transaction must be physically verified by pressing a button on the device, which prevents remote hacks.
During initialization, you will set up a PIN that adds another layer of security. For advanced users, a passphrase can also be enabled, acting as an additional “25th word” to your recovery seed. This passphrase ensures that even if someone gains access to your recovery words, they still cannot unlock your wallet without the secret phrase.
Although Trezor is highly secure, users play a crucial role in maintaining that security. Always download software only from the official trezor.io/start page, keep your recovery seed offline, and regularly update your Trezor Suite software.
One common mistake is storing recovery words as photos on a smartphone or cloud storage service. Hackers frequently target these platforms, making it unsafe. Physical offline storage is always the best choice. Similarly, beware of phishing attempts where fake websites mimic trezor.io/start.
Compared to software wallets and exchange wallets, Trezor offers unparalleled security because it keeps keys offline. Even compared to other hardware wallets, Trezor stands out for its transparency, open-source nature, and user-friendly interface.
The open-source model allows security researchers and developers worldwide to review Trezor’s code. This makes the wallet highly trustworthy, as vulnerabilities are quickly identified and patched.
Q: Can I set up Trezor without internet?
A: While you need internet to install Trezor Suite, the device itself generates and stores private keys offline, never exposing them online.
Q: What happens if I lose my Trezor device?
A: As long as you have your recovery seed, you can restore your wallet on a new Trezor or another compatible hardware wallet.
Q: Is trezor.io/start safe to use?
A: Yes, it is the official entry point for setup and updates. Always double-check the URL in your browser to ensure you are on the legitimate site.
Starting your crypto security journey with trezor.io/start is the safest and most reliable way to protect your assets. By following official steps, using Trezor Suite, and carefully safeguarding your recovery seed, you give yourself peace of mind in the volatile digital currency world. For anyone serious about cryptocurrency, Trezor is not just an option—it’s a necessity.